Singapore Drops the Name, Shifting the Game
- CRC

- Aug 14, 2025
- 5 min read
Updated: Sep 9, 2025

Introduction
Public attribution in the context of influence can be likened to an open letter, backed by technical reasoning and signed with a clear political signature. A specific incident is not only investigated but officially linked to a particular actor. Such attribution is more than a forensic statement: it is a form of strategic messaging. Public attribution always addresses a broader audience, allies, undecided third states, domestic publics, and potential future adversaries.
Attribution to UNC3886[i]
Until now, Singapore has avoided taking such a step regarding China. The previous tactic was to publish technical details and share indicators, while leaving the actual originator in the dark. This time, however, that cover was dropped[ii]: intrusions into critical infrastructure were attributed to UNC3886, a group described by Mandiant[iii] as a Chinese APT, meaning a state or state-aligned hacking group. While the statement did not explicitly mention "China," the message was clear enough to be registered.
The response followed promptly. The Chinese embassy in Singapore rejected the accusations and “courteously” offered to cooperate in the investigation.
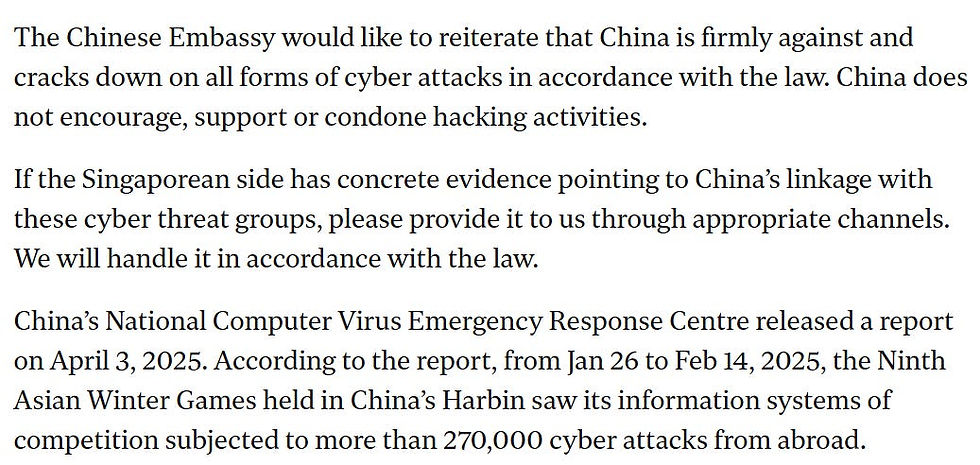
Figure 1 – Courtesy of Global Times[iv]
A short time later, the Global Times published a report by the Cybersecurity Association of China, claiming that the United States had exploited zero-day vulnerabilities in Microsoft Exchange to attack a major Chinese defence company.

Figure 2 – Courtesy of Global Times[vi]
Singapore appeared in the report only in passing, as the location of “proxy IPs.”[v]
![Figure 2 – Courtesy of Global Times[vi]](https://static.wixstatic.com/media/effca5_7095baf67be140c5a6097ee844a687a3~mv2.png/v1/fill/w_980,h_434,al_c,q_90,usm_0.66_1.00_0.01,enc_avif,quality_auto/effca5_7095baf67be140c5a6097ee844a687a3~mv2.png)
Singapore also faced a degree of backlash, albeit not particularly strong: On August 5, 2025, the Chinese embassy responded in the Straits Times “Opinion Forum”[vii] to the article published on July 25[viii], 2025, rejecting the allegations and criticizing the newspaper itself.

Figure 3 - Courtesy of Strait Times[ix]
A Facebook post on the topic followed, drawing comments and shares that made it clear the matter hit home.

Figure 4 - Courtesy of Facebook[x]
China’s Attribution Response Pattern
Instead of placing Singapore at the center of a counter-campaign, Beijing shifted the focus to its strategic rival, the United States.
It seems that Chinese reactions to attribution now follow a well-rehearsed pattern: Country X names Chinese actors; within a short time, a state-directed entity such as the CVERC (China Vulnerability Emergency Response Center)[xi] issues a report accusing the United States of having done the same. This maneuver flips the script, redirects focus, and channels the discussion into another narrative.
Noteworthy in this context is the rapid response to the SharePoint incident; the counter-report was released in about a week. In previous cases, such as Volt Typhoon (also addressed by the CVERC), reports from Chinese front organizations have taken considerably longer to surface.
It will be interesting to see how this story develops and whether we soon see a dedicated CVERC report on Singapore.
Conclusion
The public attribution of the alleged Chinese group UNC3886 by Singapore marks a notable departure from the country’s previously discreet communication style in matters of cyber threats. Instead of issuing technical reports or relying on diplomatic channels, Singapore deliberately opted for a visible public stance. This can be understood as a strategic signal, both to potential attackers and to international partners.
The effectiveness of such attributions, however, remains contested. While publicly naming an actor increases the costs for attackers, forcing them to adapt tactics or infrastructure, authoritarian states such as China often respond not by retreating, but by issuing counteraccusations. This was evident in the immediate reaction of the Chinese Embassy in Singapore. Such behaviour is particularly relevant in the context of hostile digital influence, as counteraccusations are not merely a defensive move but a deliberate attempt to reshape the narrative, cast doubt on the original claims, and undermine trust in the accuser. In these situations, attribution becomes part of a broader information conflict, where the struggle is not only over establishing technical culpability but also over influencing public perception, framing international discourse, and eroding the credibility of opposing voices.
For Singapore, this new visibility is not without risks. Attribution creates expectations, narrows the room for maneuver, and carries the potential to exacerbate tensions with China, particularly if the naming is interpreted not in isolation but as part of a broader political shift.
[Footnotes]
[i] UNC refers to "uncategorised" or "unclassified"
[ii] The Straits Times, Jaipragas, B., 2025. No idle punt: Why Singapore called out cyber saboteur UNC3886 by name. [online] Published 25 July 2025. Available at: https://www.straitstimes.com/opinion/no-idle-punt-why-singapore-called-out-cyber-saboteur-unc3886-by-name
[iii] Google Cloud Blog (Mandiant), 2024. Cloaked and Covert: Uncovering UNC3886 Espionage Operations. [online] Published 18 June 2024. Available at: https://cloud.google.com/blog/topics/threat-intelligence/uncovering-unc3886-espionage-operations?hl=en
[iv] Global Times, 2025. US intelligence uses Microsoft Exchange zero‑day vulnerabilities to attack Chinese military‑industrial enterprise’s email servers: report. [online] Published 1 August 2025, 02:24 PM. Available at: https://www.globaltimes.cn/page/202508/1339860.shtml
[v] Global Times, 2025. US intelligence uses Microsoft Exchange zero‑day vulnerabilities to attack Chinese military‑industrial enterprise’s email servers: report. [online] Published 1 August 2025, 02:24 PM. Available at: https://www.globaltimes.cn/page/202508/1339860.shtml
[vi] Global Times, 2025. US intelligence uses Microsoft Exchange zero‑day vulnerabilities to attack Chinese military‑industrial enterprise’s email servers: report. [online] Published 1 August 2025, 02:24 PM. Available at: https://www.globaltimes.cn/page/202508/1339860.shtml
[vii] The Straits Times, “Forum: China firmly against and cracks down on all forms of cyber attacks”, 2025. [online] Published 5 August 2025. Available at: https://www.straitstimes.com/opinion/forum/forum-china-firmly-against-and-cracks-down-on-all-forms-of-cyber-attacks
[viii] The Straits Times, Jaipragas, B., 2025. No idle punt: Why Singapore called out cyber saboteur UNC3886 by name. [online] Published 25 July 2025. Available at: https://www.straitstimes.com/opinion/no-idle-punt-why-singapore-called-out-cyber-saboteur-unc3886-by-name
[ix] The Straits Times, “Forum: China firmly against and cracks down on all forms of cyber attacks”, 2025. [online] Published 5 August 2025. Available at: https://www.straitstimes.com/opinion/forum/forum-china-firmly-against-and-cracks-down-on-all-forms-of-cyber-attacks
[x] Facebook, China Embassy in Singapore, 2025. Facebook post. [online] Available at: https://www.facebook.com/Chinaemb.SG/posts/1043167338010724/
[xi] The China National Computer Virus Emergency Response Center (CVERC) is a state-run institution responsible for analyzing cyber threats and coordinating national responses to viruses and software vulnerabilities. It also plays a role in China's geopolitical cyber strategy.
DISCLAIMER
Copyright and License of Product
This report (the "Product") is the property of Cyfluence Research Center gGmbH ("Cyfluence") and is protected by German and international copyright laws. The User is granted a limited, non-transferable license to use the Product solely for internal purposes. Reproduction, redistribution, or disclosure of the Product, in whole or in part, without prior written consent from Cyfluence is strictly prohibited. All copyright, trademark, and proprietary notices must be maintained.
Disclaimer of Warranties
The Product is provided "as is" without warranties of any kind, express or implied, including but not limited to warranties of merchantability or fitness for a particular purpose. Although Cyfluence takes reasonable measures to screen for viruses and harmful code, it cannot guarantee the Product is free from such risks.
Accuracy of Information
The information in the Product has been obtained from sources believed to be reliable. However, Cyfluence does not guarantee the information's accuracy, completeness, or adequacy. The User assumes full responsibility for how they use and interpret the Product. Cyfluence is not liable for errors or omissions; opinions may change without notice.
Limitation of Liability
To the fullest extent permitted by law, Cyfluence shall not be liable for any direct, indirect, incidental, or consequential damages, including lost profits or data, arising from the use of or inability to use the Product, even if advised of such possibilities. Liability for intent or gross negligence remains unaffected under German law.
Indemnification
The User agrees to indemnify and hold harmless Cyfluence, its affiliates, licensors, and employees from any claims or damages arising from the User’s use of the Product or violation of these terms.
Third-Party Rights
The provisions regarding Disclaimer of Warranties, Limitation of Liability, and Indemnification extend to Cyfluence, its affiliates, licensors, and their agents, who have the right to enforce these terms.
Governing Law and Jurisdiction
This Agreement is governed by German law, and any disputes shall be resolved exclusively in the courts of Berlin. If any provision is found invalid, the remaining terms remain in full effect.
_edited.png)
.png)


